Project Overview
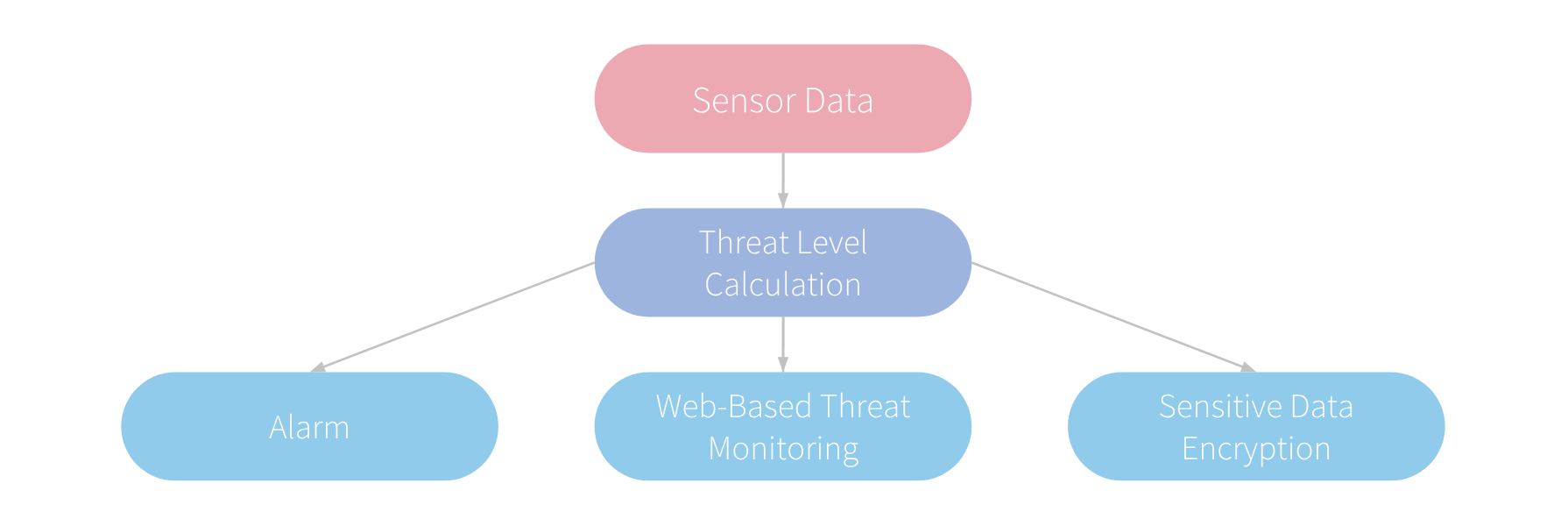
The Protected IoT Security and Threat Analysis/Response (PI-STAR) is an IoT-based security system designed to provide wireless security to a room with confidential information. It uses a variety of sensor modules to determine the threat level and probability of a compromising incident within a room. The system then displays real-time attack and threat level information on a web interface for continuous monitoring. Additionally, the system uses advanced security to protect against both cyber and physical attacks. Finally, the system is able to respond to critical threats by triggering an alarm and encrypting sensitive information on an external medium.
The system consists of sensor modules throughout the room as well as within the box node containing the sensitive information.
PI-STAR was created by Ibiyemi Abiodun, Simon Abrelat, Sidhesh Desai, and Grace Pfohl as part of an internship at the Georgia Tech Research Institute CIPHER-TMPO Lab.